Rclone setup on Raspberry Pi - Part 1
January 22, 2021 | StackThere are a lot of backup tools available out there and depending on what the goal is, one should consider what meets the needs. Basically there are different kinds of backup setups:
- Client-side backup solutions (applications on your devices), few devices
- Server/agent (central server and a script on the clients), many devices
- Enterprice systems (with tape backup capabillities etc.) many devices with a high integrity level
- Agentless (does not need to be installed on clients) servers and cloud
Rclone is agentless and the reason this solution fits my personal needs are the following: My phone, labtop etc. is already synced to a server. But, I have a lot of servers running, so making sure that the vital data is backed up on a regular basis is important for me. I'm not talking about system images, where one should be able to restore a full system. I will always be able to do that manualy or via tools like Ansible, but the vital data on those systems, I can't restore if it is not backed up.
Following the installation instructions from rclone.org:
curl https://rclone.org/install.sh | sudo bashor
sudo (snap/apt) install rclone (but currently aptitude will currently only install version 1.45 which is without GUI)
If using Ansible Stefan Weichinger has made a role here to deploy Rclone.
After a succesful install, run the config command:
rclone configYou will start by setting up a "New remote". Rclone has a huge library of connection modules to external storage providers, in contrast to ex. rsync and other sync/backup solutions.
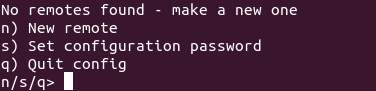
Choose "n" for new and next you will provide a "name".
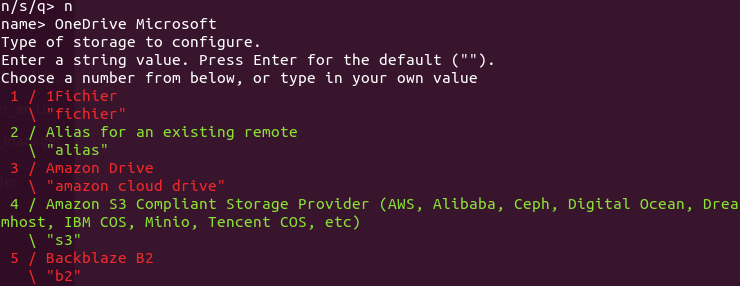
Choose the storage type. As I am using a headless install of RPi (you should consider installing a desktop version/GUI, if you want to use OneDrive to enable VCN), the configurations might be different for some of the modules.
After adding different hosts to your configuration. There is of cause a hugh amount of usefull commands to learn and Rclone has always been a CLI application, but that is starting to change now. A new experimental GUI is being developed at this moment and we will try it out.
Rclone Web GUI
If you are installing on a labtop, you can start the GUI service by typing the following command in the console.
rclone rcd --rc-web-guiand go to http://localhost:5572
But, let's try and get a GUI accessible on the local network. First we need to make the connection to the GUI encrypted with a selfsigned certificate (that will give you a browser warning, but we assume that you trust your self in this case).
sudo openssl req -newkey rsa:2048 -x509 -sha256 -days 3650 -nodes -out /etc/ssl/certs/backup-server.crt -keyout /etc/ssl/private/backup-server.keyIf you have an Apache server running, you will be able to create a user and password to access the web GUI with this command (not nessesary only if you already have Apache running):
sudo htpasswd -c /home/<path>/.htpasswd <username>otherwise you create the user and password at launch. There are different flags to apply when initializing the web GUI:
--rc-web-gui (the first command that checks for all of the following)
--rc-web-gui-update (check for updates)
--rc-web-gui-force-update (if something is broken in the install)
--rc-web-gui-no-open-browser (prevent the browser to launch automatically)
--rc-user <username> (if you don't use Apache)
--rc-pass <random password> (if you don't use Apache)
--rc-serve (serving remote objects thru http://)
--rc-addr :443 (serve encrypted over https://)
--rc-htpasswd /path/to/htpasswd (path to password file)
--rc-cert /path/to/ssl.crt
--rc-key /path/to/ssl.key
So, let's try to start the web GUI. In this case on a Pi with no webserver installed.
sudo rclone rcd --rc-web-gui --rc-web-gui-update --rc-web-gui-no-open-browser --rc-user test --rc-pass test --rc-serve --rc-cert /etc/ssl/certs/backup-server.crt --rc-key /etc/ssl/private/backup-server.key --rc-addr=192.168.68.124:5572
(change the IP to your Pi's)Here we:
- load the GUI
- Check for updates
- Prevent browser from auto loading
- Create a username
- Create password
- Setup a server
- Point to our certificate and key
- And last we specify which port and address the server is listening on.
And voila! Access your backup control center at you choosen port (you browser may complain that it does not trust you, as a Certificate Authority so you need to approve the connection).
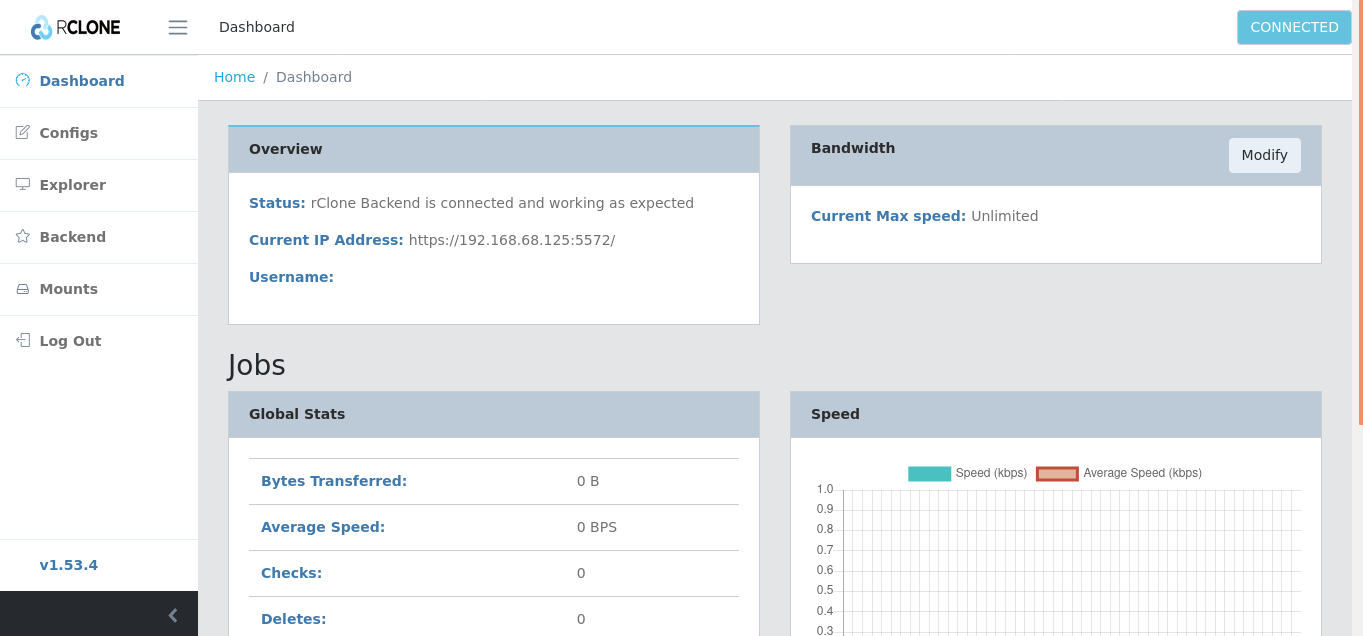
OneDrive - Rclone
Now, as a headless install you might try the auto install for OneDrive (and follow the instructions at rclone, It did'nt work for me). So, I had to connect to the Pi with VNC and do the setup. Alternatively you could try and make an app access at Azure, with the right priviledges.
Important: After you get a "success" in the browser screen, go back to terminal and finish the install.
Continue setting up access to all the locations you need backup to and from...
Security considerations
Basically rclone is relativ secure, if all communications channels are encrypted and your backups are encrypted. But, in this case I use a Raspberry Pi and an SD-card which is not encrypted. So, any physical access to the Pi is problematic from a security perspective. There seems to have been developed a solution for secure boot by Swissbit who have different products, but otherwise you have to limit the access to your Pi.
Alternatively, there is an option in rclone to encrypt the .rclone.conf that counter messures this risk by encrypting the config file with access privileges to your "remotes", which I'll try to implement in the following.
- We want to make it very difficult to access our creditentials (to cloud storage and servers), if someone should get their hands in our RPi's SD-card. So, we will encrypt the .rclone.conf.
- We will try to setup a method to do auto-authentication as long as the Pi is connected to power. So, we don't have to supply the password for decryption, more than once (after first boot and keep the password in memory)
Encryption module
To enable the encryption module for the .rclone.conf:
rclone configand choose "Set configuration password" and follow the instructions. Don't loose your strong password!
---------
There are probably other methodes to do the following, I tried a bit of different solutions like screen and tmux sessions, that would be mounted in ex. a crontab. But, assuming that the risk for physical access to your Pi is higher, than virtual access! The following may be a better solution. But, be aware that in generel you would not do this in any public accessible system or systems with multi purpose or multiple user accounts, as the password for decrypting the config file will be stored unencrypted in the /tmp/ folder which means that all applications can decrypt the config file. The good thing is that the /tmp/ directory is a tmpfs "format" and therefore temporary, so in case of reboot, theft of SD-card etc. the password will not be accessible anymore.
---------
Make a script called ex. setup_password.sh in your home folder:
#!/bin/bash
# setup_password.sh
if [[ ! -e /tmp/rc_p.txt ]]; then
echo -n "Type the password for rclone: ";
read;
echo ${REPLY} > /tmp/rc_p.txt
fiThe above script has to be executed every time your reboot your system, it will make the temporary password file. Make sure to make it executable (chmod 700 setup_password.sh). After that we want to make a system wide accesable environment variable so "sudo nano /etc/profile" and past this line in the bottum of the file:
# Check if password exists
if [ -f "/tmp/rc_p.txt" ]; then
export RCLONE_CONFIG_PASS=`cat /tmp/rc_p.txt`
fiSo, the first time after reboot of if somehow the rc_p.txt has gone execute your script as the first thing before using rclone:
./setup_password.sh
(and afterwards)
source /etc/profile (to reload for the current profile)
Now, we would like to get notifications if something fails on our backup server.
Follow this post to setup mail capabillity of you Pi..
If you choose to setup mail notification for your backupsolution, you could create a directory for mails in the home dir:
mkdir ~/mailsIn this directory create a new file called: "missing_config_pass.txt"
nano ~/mails/missing_config_pass.txtand write some content like:
Subject: The Backup server is missing decrypt pass for rclone
Access the server and run the setup_password.sh, with the correct phrase. The backup server will be down, untill this issue is resolved.and make a test: sendmail your_mail@address.com < /path/mails/missing_config_pass.txt and with a bit of luck something like this should arrive in your mailbox.
The last thing we have to do, is to figure out if the environment variable has been set. All scripts in the directory /etc/profile.d/ will be executed everytime a new session is started. So, putting the script there would propably also be more ideal, but it could also be a cron job running once each 24th hour.
But, let's continue to use our profile script. The following would check if the environment variable is set and if not, it will send an e-mail it's a continuation of our /etc/profile script, it will now look like this:
# Check if password exists
if [ -f "/tmp/rc_p.txt" ]; then
export RCLONE_CONFIG_PASS=`cat /tmp/rc_p.txt`
else
sendmail your_mail@address.com < /home/pi/mails/missing_config_pass.txt
fiIF everything has worked out for your so far (you probably had some debugging if this post is more than one year old). You actually have the basics for a completly independent backup system, that can rest on a 50 $ Raspberry Pi.
Of cause your would probably also setup some kind of cron job to see if your Pi is alive. It is not unreasonably to think that your dog might bite over the power cable (or your kids or wife for that matter).
I'll write another article about Rclones more specific features, when applied as a backup solution...