OPNsense ProtonVPN setup
November 11, 2021 | StackIf you have a desent firewall, having some dedicated interfaces with VPN from the firewall out may be a great idea because it can help with.
- Saving a lot of resources on the individual devices that othervise had to do all the encryption them selves.
- Saving money on account with limited allowed devices.
- Using VPN for divices that might not support it by their own.
- Having additional safety layer for annonymizing, if other fails.
- Providing easy access for VPN and annonymizing, without the hasle of configuration.
This may look similar for other VPN services, but you might supply this tutorial with other information they have provided typically with a Pfsense setup. Start by logging in to your VPN provider, here you will have access to all nessesary information for the following setup.
Certificate Authority
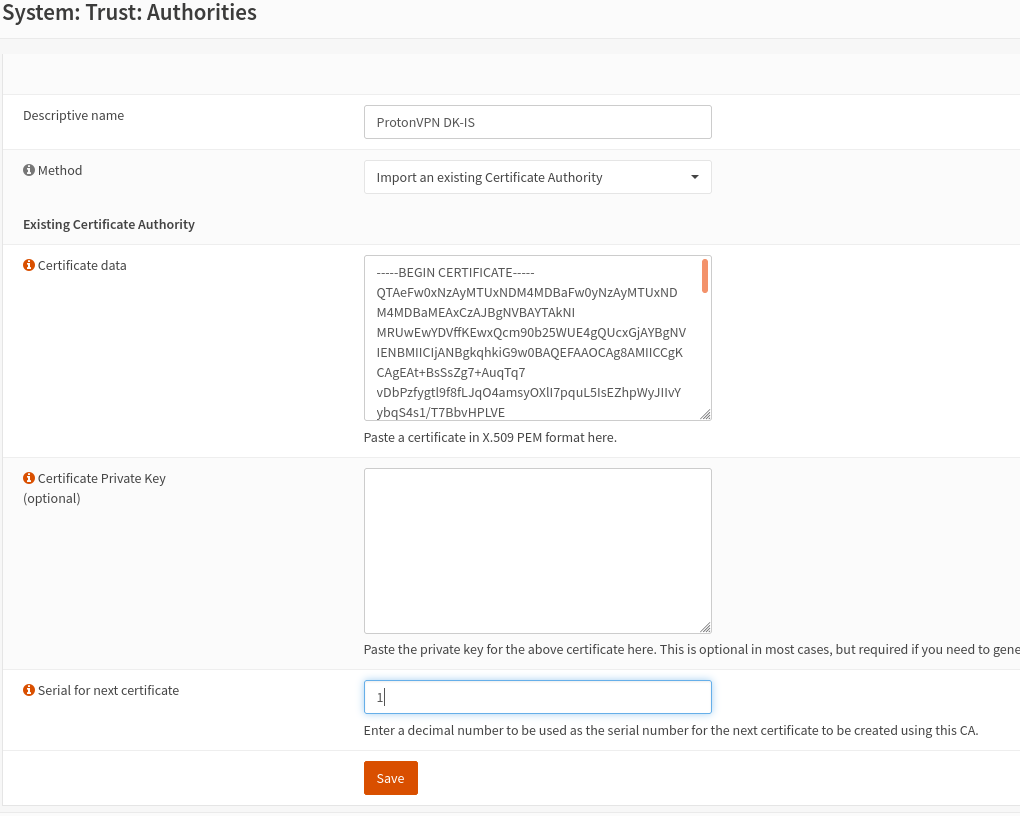
In OpnSense then go to System -> Trust -> Authorities -> "+"
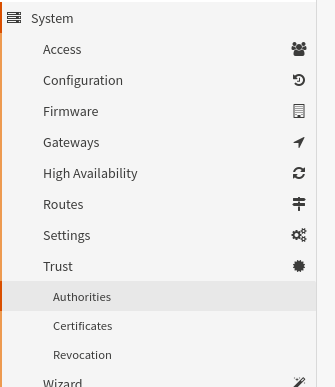
Download configuration file:
Login to your VPN service account and download your country's exit server (you might also download multiple files from neighboring countries for failover, that I'll explain later).
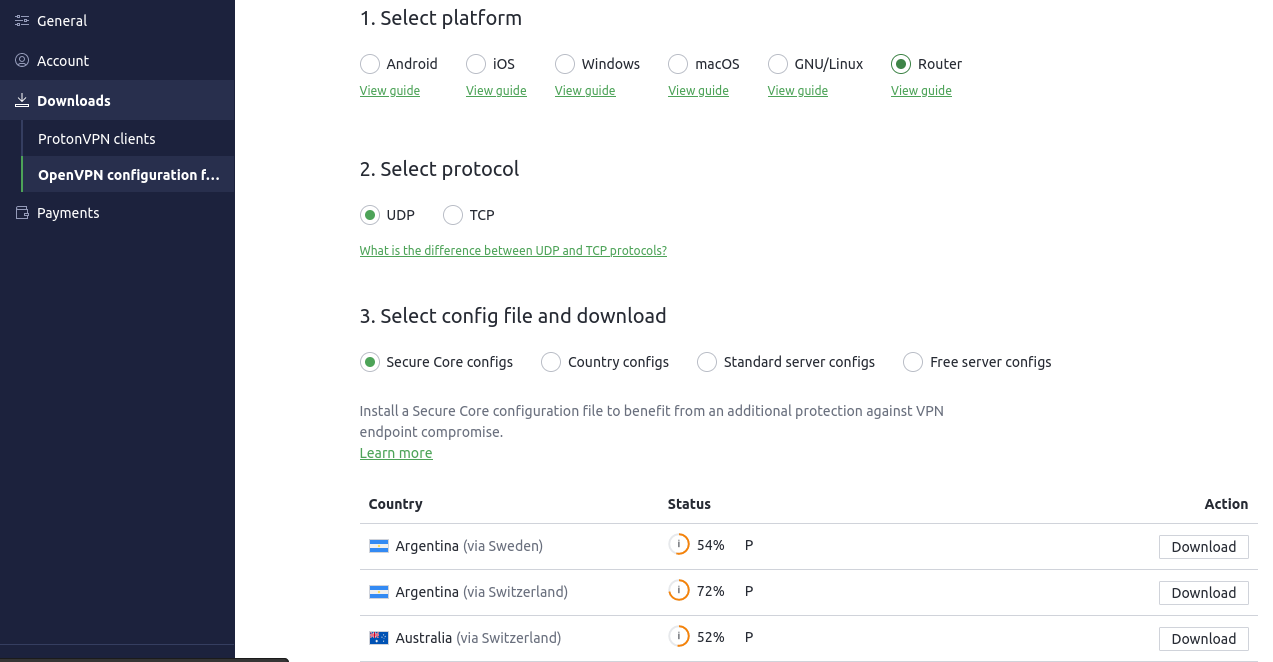
Copy the certificate from one of the config files:
and paste it to the field "Certificate data" and give it a description:
Adding VPN Client
Go to VPN -> OpenVPN -> Clients -> "+" to add a new client:
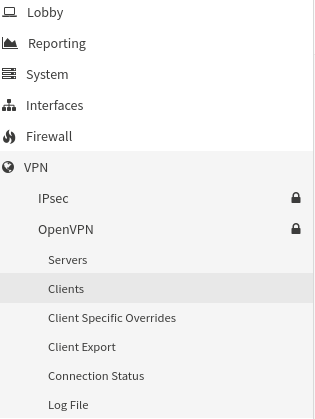
Adding details from all of the downloaded configuration files, they will have different server depending on the exit server:
- Fill in the description (here you could add specifics about exit server and core)
- Fill in the remote servers/server and if you have choosen UDP use default port 1194, this would work as failover is one server is down.
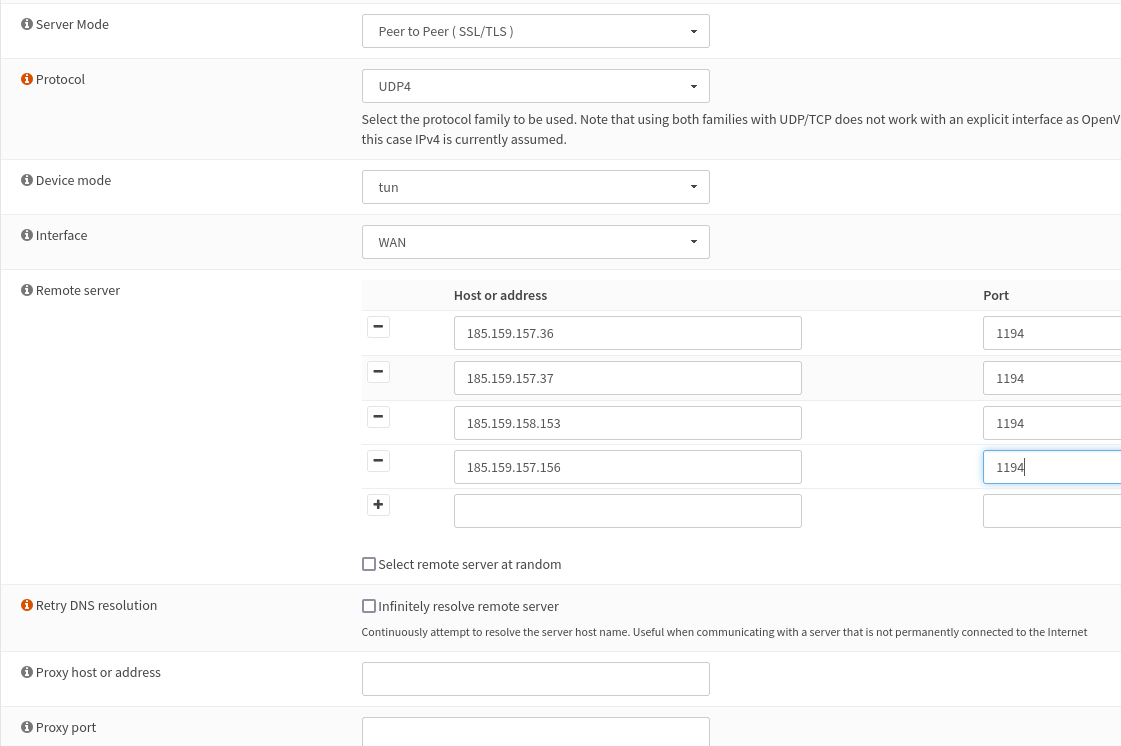
3. Username can contain operators: ":0" is forcing to user exit server (not sure if this is really nessesary), "+f2" will filter malware and ads, "+f1" will only filter malware but allow ads.
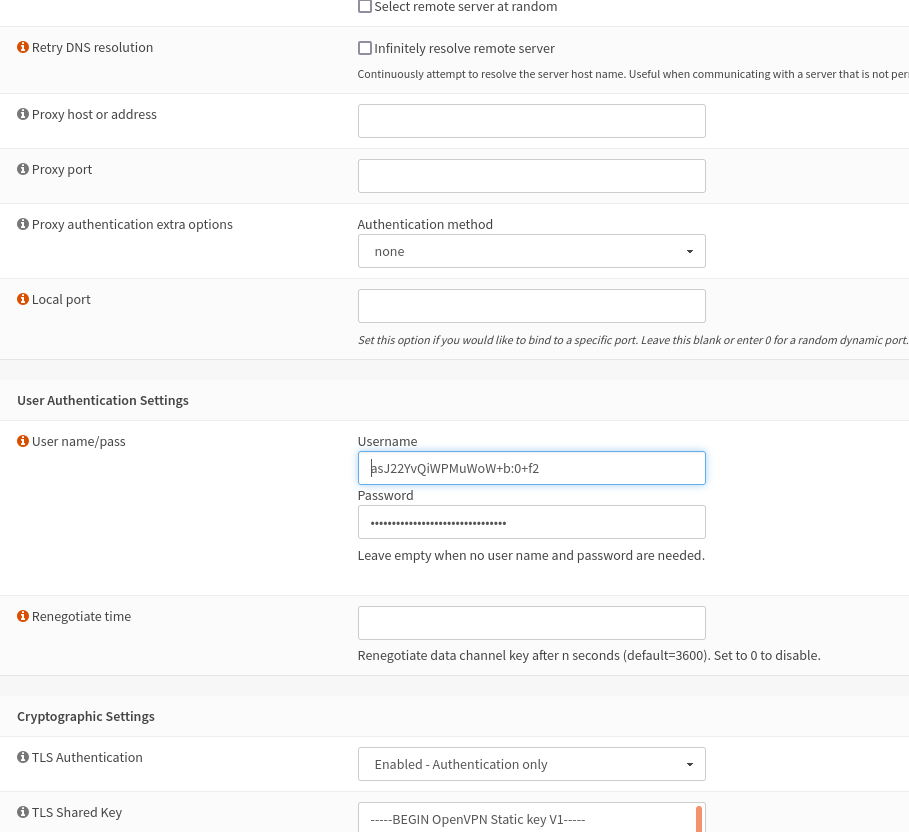
4. Enabled - Authentication only
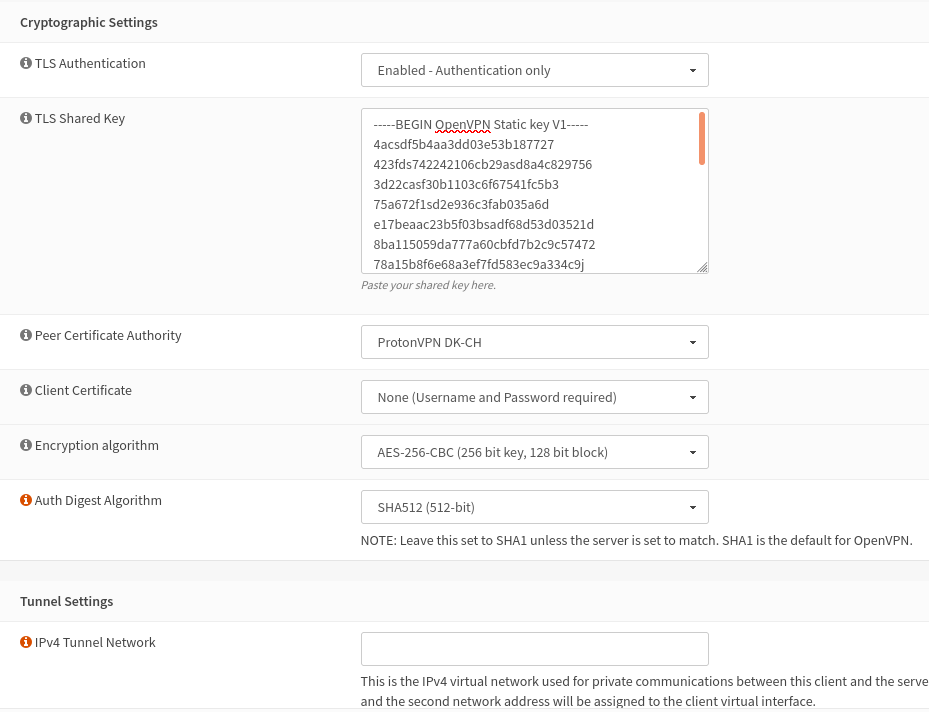
5. Insert the TLS Shared Key (including -----BEGIN and -----END), from the config file.
6. Choose the CA you made earlier and choose the same selections as in the screendump.
Don't do anything in the Tunnel section.
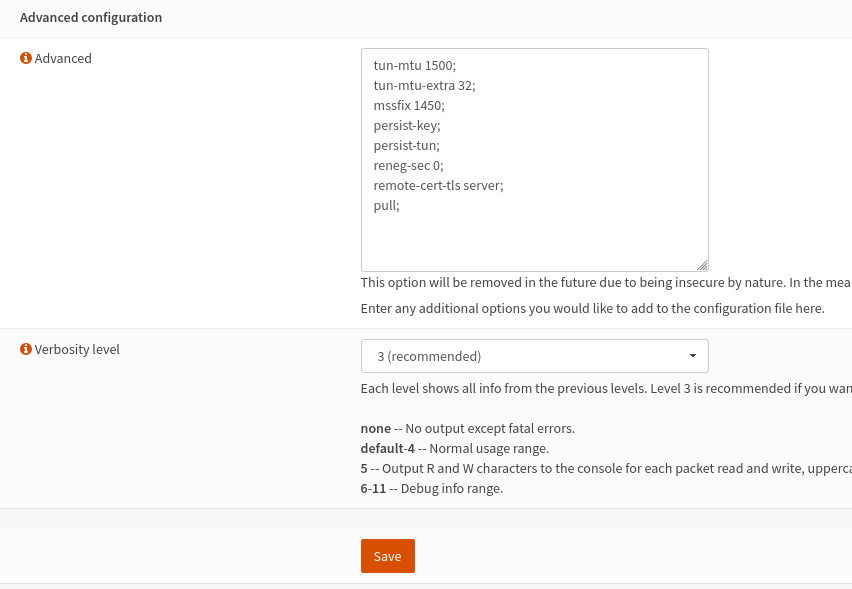
7. Paste the following in the Advanced field:
tun-mtu 1500;
tun-mtu-extra 32;
mssfix 1450;
persist-key;
persist-tun;
reneg-sec 0;
remote-cert-tls server;
pull;8. Verbosity level set to 3
Under VPN -> OpenVPN -> Connection Status, you should be able to see the connection is "up". You might try to reload it. If it is still trying to connect, continue to next step (I had this issue, when setting up multiple VPN services as failover and it should be solved with the next step.)
Attach the interface
Assign the new interface:
Edit Interface
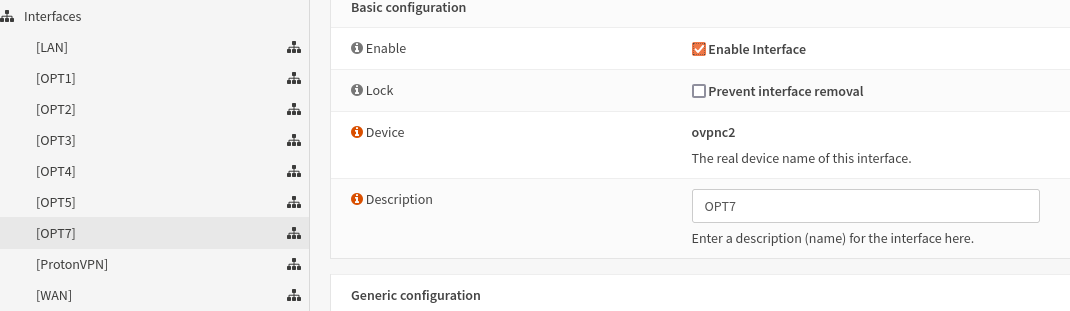
- Enable interface
- Give it a description
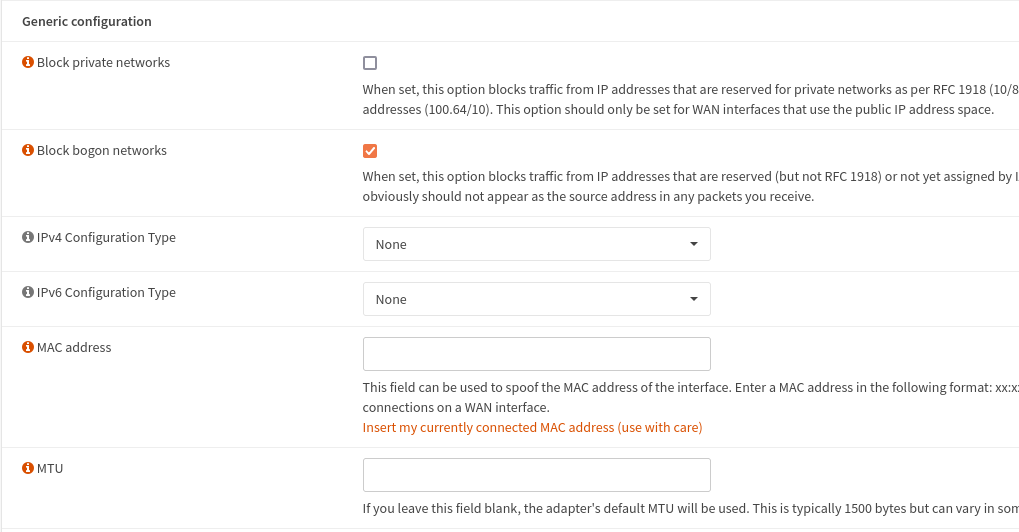
- Check the "Block bogon networks" and hit "Save" button.
Create a Gateway
Under System -> Gateways -> Single. Create a new gateway:
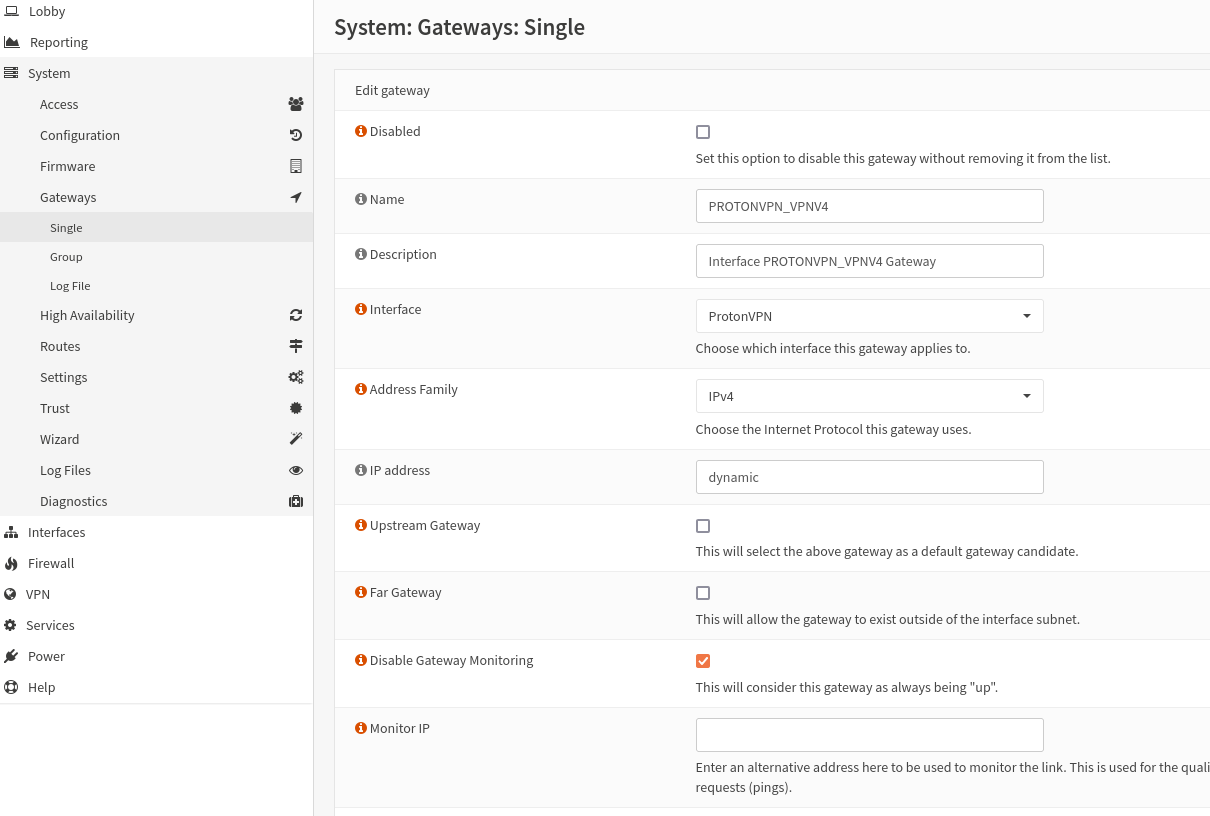
- Choose Name, description and interface. Keep the settings as above and hit "Save".
NAT
Go to Firewall -> NAT -> Outbound and change the mode to "Hybrid":
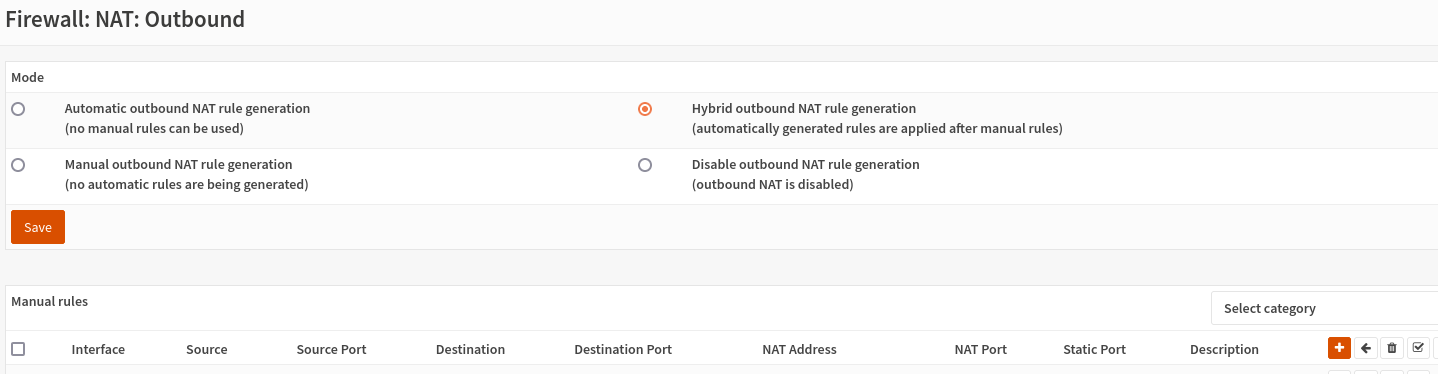
Add a new Outbound rule, that looks similar to this:
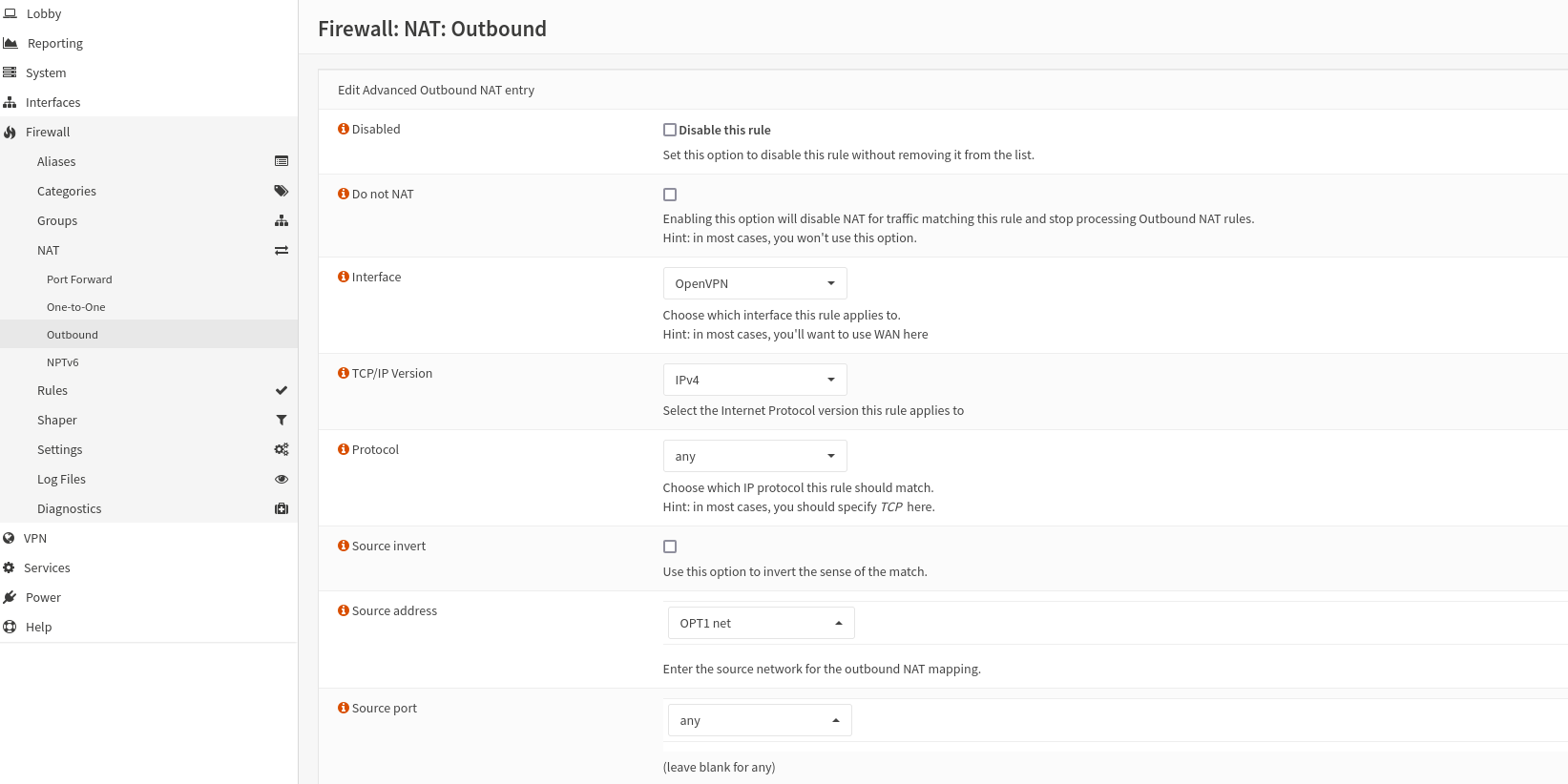
- "Interface" should be changed to you VPN connection
- Select the interface that should have VPN under the "Source address"
And hit save..
Other rules that
Now, i have had some troubleshooting here. Under all LAN's (except the one with VPN) i have selected "default" under "Gateway" and expected them to use the default gateway, which is not the VPN. Even thou I have set priority on the gateways, this seemed to continuosly cause trouble. So, if you run into trouble here go to each LAN and select the propper specific gateway (in below case should be "WAN_DHCP"):
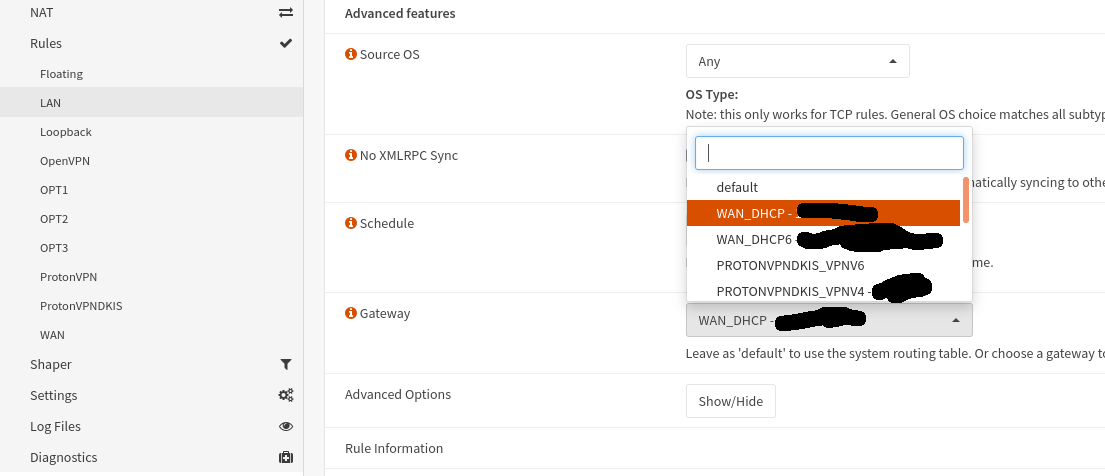
And for the interface we NATted you will choose your VPN connection as gateway and that should be it.
Failover (with multiple VPN providers)
The following is to try and make failover if one provider is overloaded or down, then we will automatically try another.
Follow all the above steps to setup another VPN provider.
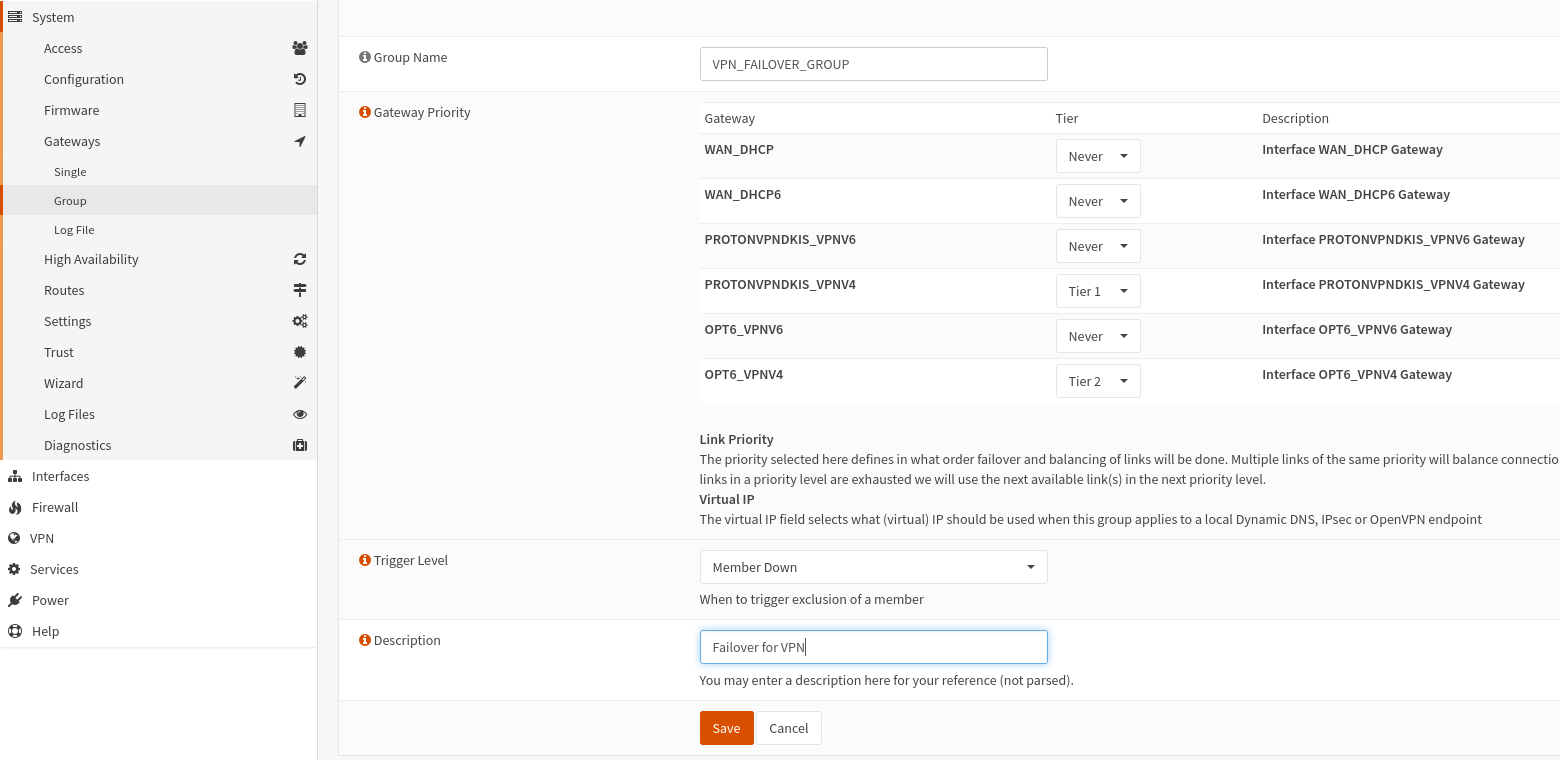
Go to System -> Gateways -> Group -> "+" and make a group as above. Where "Tier 1" is the first attempted connection and "Tier 2" is the failover. You could have many of these, and if you depend on HA on your connection it might be a good way to achieve this.
Under Firewall -> Rules -> (interface), you choose the group as "Gateway"
Additional settings
Go to System -> Gateways -> Single and disable the IPv6 gateway for the VPN as it isn't used.
DNS leak
Additionally Proton recommends changing DNS provider. Go to System -> Settings -> General and add Protons own DNS 10.1.0.1 and add it to the VPN interface.
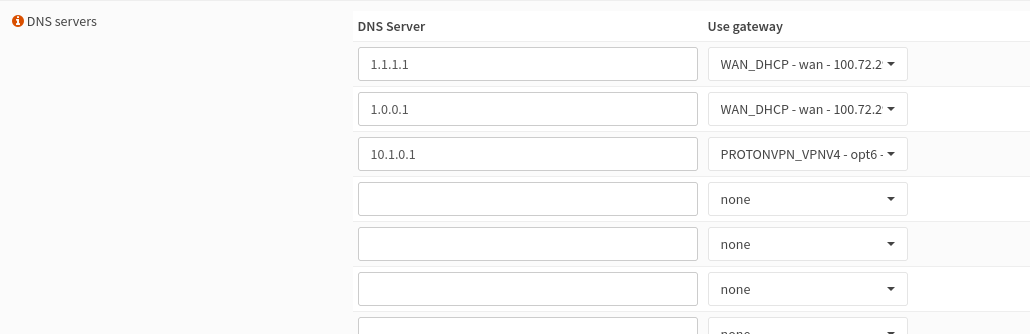
you may also have a look at the section "DNS server options" below. But this were sufficient in my case.
Test if you have DNS leak: https://www.dnsleaktest.com/
Troubleshooting
It seems DNS leaks can cause trouble. Test out the above mentioned "DNS server options" with different settings.
But, most likely: I had set Cloudflare as DNS provider in Firefox, after disabling that everything turned out fine. Secondly go to your networksettings and individual connection settings, and see if you have provided a specific DNS provider here.